AppSec that thinks like an attacker and keeps up with your best developers
Leading security teams use Kodem to find, fix and defend the 5% of vulnerabilities that attackers can exploit in their environment - reducing triage and remediation time to near zero.
Trusted by
















































Designed with attacker's playbook in mind
Low and medium CVEs are ignored
Legacy tools flood teams with alerts. Real threats get buried.
Exploiting one layer leads to the next
From libraries to containers to runtime, exploits span the stack.
Not all risk is reachable
Context matters. Production determines what can be compromised.
See the exploit. Fix the code. Stop the attack.
1
Runtime SCA
Know which open source packages are actually used in production
2
Runtime SAST
Identify which vulnerable functions execute in your environment
3
ADR (Application Detection & Response)
Detect and stop attack chains before they are used
4
Runtime Intelligence
Prioritize CVEs based on exploitability, reachability, and runtime behavior
5
Meet Kai: Your AppSec Agent
Thinks like an attacker, acts like a security engineer, and writes fixes—even when there’s no public patch available.
Break attack chains early
Attackers move through your stack. Kodem maps how vulnerabilities connect so you can stop the chain at the first link.


Fix what's real, not what's listed
Kodem automates application security workflows, saving 400 person-hours per codebase. Using runtime Intelligence, Kodem delivers the attacker's perspective of an application and focuses on real, exploitable vulnerabilities across the application stack.
Deploy instantly. No restarts. No disruption.
Kodem deploys in minutes as an agentless eBPF‑based sensor that attaches to your containers and hosts, no code changes, no restarts, and under 1 % performance overhead. By running alongside your application, it delivers full runtime visibility while engineering keeps shipping at full velocity, preserving uptime across Kubernetes, VMs, and serverless environments.
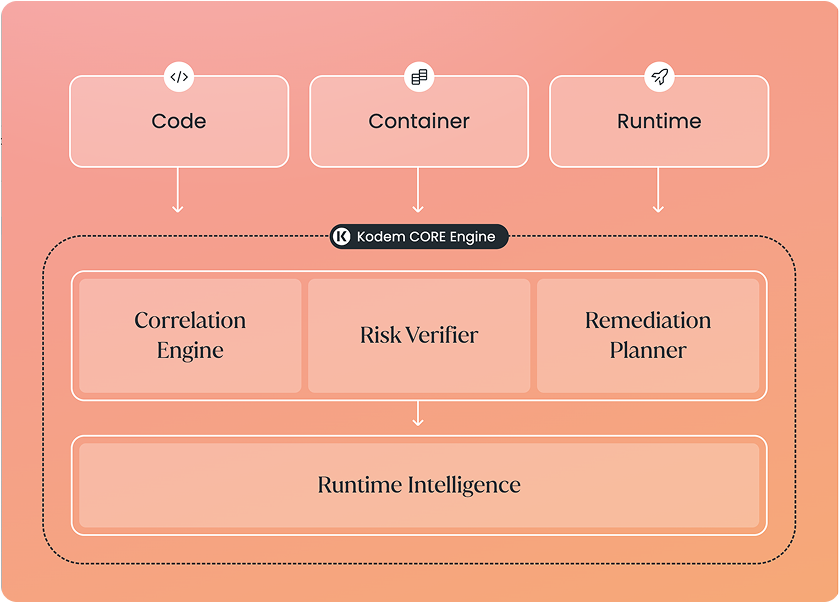
Kodem addresses your biggest AppSec challenges
Fragmented tools & inventories
Weak prioritization, manual triage
Start seeing what matters
Featured posts

Attack chain methodology
The rapid digitalization of businesses has brought application security to the forefront of organizational priorities. However, despite significant investments in security tools and technologies, data breaches and cyberattacks continue to occur alarmingly. This blog explores the root causes of this disconnect, focusing on the misalignment between traditional AppSec approaches and the methods employed by attackers. It underscores the need for a shift in security strategies to align more closely with real-world threats and attack methodologies.

Runtime intelligence, meet AI
Kodem’s runtime intelligence is a game changer for vulnerability management and open source security. It allows security practitioners to gain deep visibility into how their applications interact by analyzing what components are in use and how data moves within them to expose only real risk. Developers can focus on real threats, empowered by automatic risk scoring and triaging processes and built-in false positives elimination.

Redefine application security with Kodem & Google Cloud
Proactively detect and mitigate cloud security vulnerabilities, streamline application security workflows, and build a developer-centric culture. With runtime-powered security from Kodem and Google Cloud, secure your cloud applications, containers, source code, and more.
